Provenance
Die Provenance beschreibt als Meta-Ressource die Herkunft einer Einwilligung. Neben Details zu den enthaltenen Unterschriften (Wer hat ggf. für Wen Wann und auf Welche Weise unterzeichnet), stellt die Provenance ebenfalls den Bezug zum Scan der Einwilligung her.
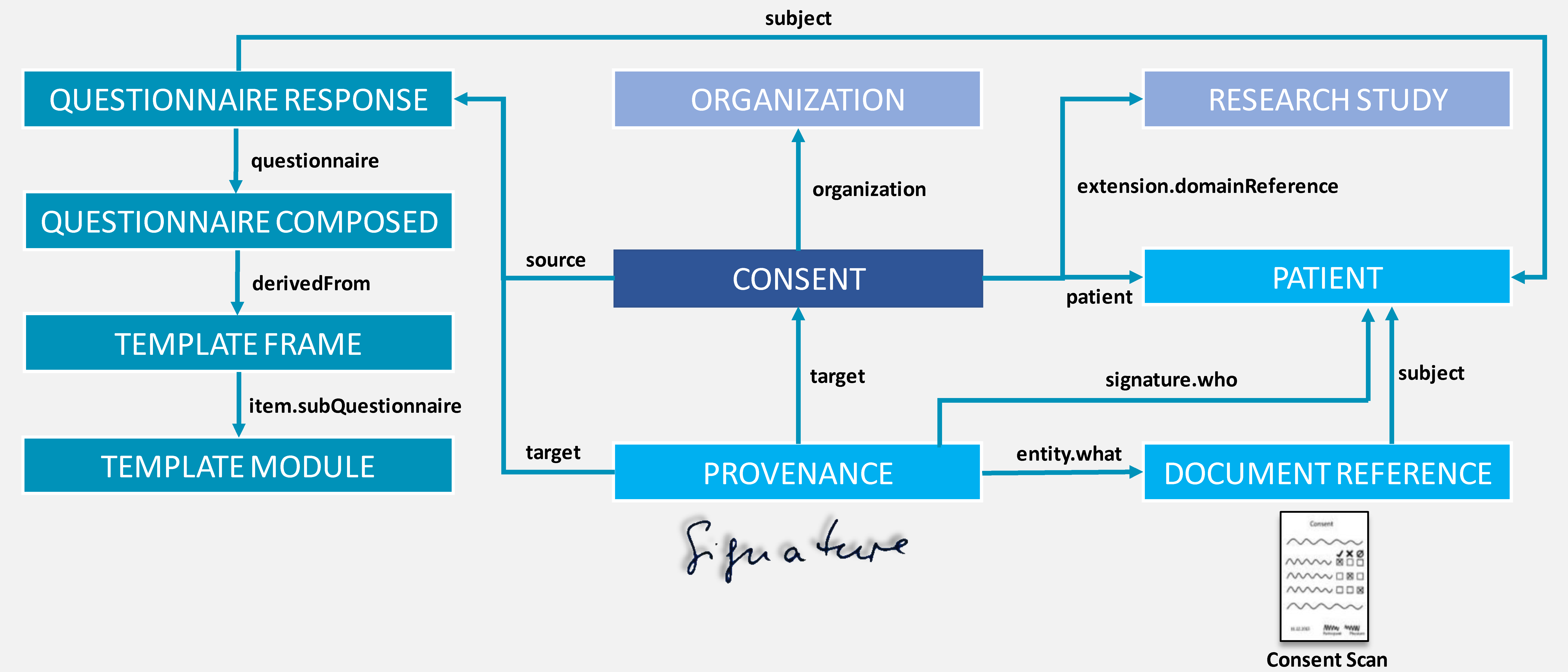
Der Provenance.Agent wird genutzt, um die verwendete Software (z.B. gICS) oder die an der Erstellung der Einwilligung beteiligten Personen und/oder Organisationen zu referenzieren.
Die Art der Unterschrift wird wie folgt angegeben. Weitere SignatureTypes sind möglich.
| Art der Unterschrift | System | Code | Display |
|---|---|---|---|
| Unterschrift der einwilligenden Person | urn:iso-astm:E1762-95:2013 | 1.2.840.10065.1.12.1.7 | Consent Signature |
| Unterschrift der (gesetzlich) vertretenden Person | urn:iso-astm:E1762-95:2013 | 1.2.840.10065.1.12.1.11 | Consent Witness Signature |
| Unterschrift der aufklärenden Person | urn:iso-astm:E1762-95:2013 | 1.2.840.10065.1.12.1.5 | Verification Signature |
| ConsentManagementProvenance (Provenance) | C | Provenance | There are no (further) constraints on this element Element idProvenanceShort description Who, What, When for a set of resources Alternate namesHistory, Event, Activity DefinitionProvenance of a resource is a record that describes entities and processes involved in producing and delivering or otherwise influencing that resource. Provenance provides a critical foundation for assessing authenticity, enabling trust, and allowing reproducibility. Provenance assertions are a form of contextual metadata and can themselves become important records with their own provenance. Provenance statement indicates clinical significance in terms of confidence in authenticity, reliability, and trustworthiness, integrity, and stage in lifecycle (e.g. Document Completion - has the artifact been legally authenticated), all of which may impact security, privacy, and trust policies. Some parties may be duplicated between the target resource and its provenance. For instance, the prescriber is usually (but not always) the author of the prescription resource. This resource is defined with close consideration for W3C Provenance.
| |||
| id | Σ | 0..1 | string | There are no (further) constraints on this element Element idProvenance.idShort description Logical id of this artifact DefinitionThe logical id of the resource, as used in the URL for the resource. Once assigned, this value never changes. The only time that a resource does not have an id is when it is being submitted to the server using a create operation. | ||
| meta | Σ | 0..1 | Meta | There are no (further) constraints on this element Element idProvenance.metaShort description Metadata about the resource DefinitionThe metadata about the resource. This is content that is maintained by the infrastructure. Changes to the content might not always be associated with version changes to the resource. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| implicitRules | Σ ?! | 0..1 | uri | There are no (further) constraints on this element Element idProvenance.implicitRulesShort description A set of rules under which this content was created DefinitionA reference to a set of rules that were followed when the resource was constructed, and which must be understood when processing the content. Often, this is a reference to an implementation guide that defines the special rules along with other profiles etc. Asserting this rule set restricts the content to be only understood by a limited set of trading partners. This inherently limits the usefulness of the data in the long term. However, the existing health eco-system is highly fractured, and not yet ready to define, collect, and exchange data in a generally computable sense. Wherever possible, implementers and/or specification writers should avoid using this element. Often, when used, the URL is a reference to an implementation guide that defines these special rules as part of it's narrative along with other profiles, value sets, etc. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| language | 0..1 | codeBinding | There are no (further) constraints on this element Element idProvenance.languageShort description Language of the resource content DefinitionThe base language in which the resource is written. Language is provided to support indexing and accessibility (typically, services such as text to speech use the language tag). The html language tag in the narrative applies to the narrative. The language tag on the resource may be used to specify the language of other presentations generated from the data in the resource. Not all the content has to be in the base language. The Resource.language should not be assumed to apply to the narrative automatically. If a language is specified, it should it also be specified on the div element in the html (see rules in HTML5 for information about the relationship between xml:lang and the html lang attribute). A human language.
The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| |||
| text | 0..1 | Narrative | There are no (further) constraints on this element Element idProvenance.textShort description Text summary of the resource, for human interpretation Alternate namesnarrative, html, xhtml, display DefinitionA human-readable narrative that contains a summary of the resource and can be used to represent the content of the resource to a human. The narrative need not encode all the structured data, but is required to contain sufficient detail to make it "clinically safe" for a human to just read the narrative. Resource definitions may define what content should be represented in the narrative to ensure clinical safety. Contained resources do not have narrative. Resources that are not contained SHOULD have a narrative. In some cases, a resource may only have text with little or no additional discrete data (as long as all minOccurs=1 elements are satisfied). This may be necessary for data from legacy systems where information is captured as a "text blob" or where text is additionally entered raw or narrated and encoded information is added later. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| |||
| contained | 0..* | Resource | There are no (further) constraints on this element Element idProvenance.containedShort description Contained, inline Resources Alternate namesinline resources, anonymous resources, contained resources DefinitionThese resources do not have an independent existence apart from the resource that contains them - they cannot be identified independently, and nor can they have their own independent transaction scope. This should never be done when the content can be identified properly, as once identification is lost, it is extremely difficult (and context dependent) to restore it again. Contained resources may have profiles and tags In their meta elements, but SHALL NOT have security labels.
| |||
| extension | C | 0..* | Extension | There are no (further) constraints on this element Element idProvenance.extensionShort description Additional content defined by implementations Alternate namesextensions, user content DefinitionMay be used to represent additional information that is not part of the basic definition of the resource. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer can define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. Unordered, Open, by url(Value) Extensions are always sliced by (at least) url ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| modifierExtension | ?! C | 0..* | Extension | There are no (further) constraints on this element Element idProvenance.modifierExtensionShort description Extensions that cannot be ignored Alternate namesextensions, user content DefinitionMay be used to represent additional information that is not part of the basic definition of the resource and that modifies the understanding of the element that contains it and/or the understanding of the containing element's descendants. Usually modifier elements provide negation or qualification. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer is allowed to define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. Applications processing a resource are required to check for modifier extensions. Modifier extensions SHALL NOT change the meaning of any elements on Resource or DomainResource (including cannot change the meaning of modifierExtension itself). Modifier extensions allow for extensions that cannot be safely ignored to be clearly distinguished from the vast majority of extensions which can be safely ignored. This promotes interoperability by eliminating the need for implementers to prohibit the presence of extensions. For further information, see the definition of modifier extensions. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. Unordered, Open, by url(Value) Extensions are always sliced by (at least) url ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| target | S Σ C | 1..* | Reference(ConsentManagementConsent | ConsentManagementQuestionnaireResponse) | Element idProvenance.targetShort description Target Reference(s) (usually version specific) DefinitionThe Reference(s) that were generated or updated by the activity described in this resource. A provenance can point to more than one target if multiple resources were created/updated by the same activity. Target references are usually version specific, but might not be, if a version has not been assigned or if the provenance information is part of the set of resources being maintained (i.e. a document). When using the RESTful API, the identity of the resource might not be known (especially not the version specific one); the client may either submit the resource first, and then the provenance, or it may submit both using a single transaction. See the notes on transaction for further discussion. Reference(ConsentManagementConsent | ConsentManagementQuestionnaireResponse) ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| id | 0..1 | string | There are no (further) constraints on this element Element idProvenance.target.idShort description Unique id for inter-element referencing DefinitionUnique id for the element within a resource (for internal references). This may be any string value that does not contain spaces.
| |||
| extension | C | 0..* | Extension | There are no (further) constraints on this element Element idProvenance.target.extensionShort description Additional content defined by implementations Alternate namesextensions, user content DefinitionMay be used to represent additional information that is not part of the basic definition of the element. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer can define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. Unordered, Open, by url(Value) Extensions are always sliced by (at least) url ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| reference | S Σ C | 1..1 | string | There are no (further) constraints on this element Element idProvenance.target.referenceShort description Literal reference, Relative, internal or absolute URL DefinitionA reference to a location at which the other resource is found. The reference may be a relative reference, in which case it is relative to the service base URL, or an absolute URL that resolves to the location where the resource is found. The reference may be version specific or not. If the reference is not to a FHIR RESTful server, then it should be assumed to be version specific. Internal fragment references (start with '#') refer to contained resources. Using absolute URLs provides a stable scalable approach suitable for a cloud/web context, while using relative/logical references provides a flexible approach suitable for use when trading across closed eco-system boundaries. Absolute URLs do not need to point to a FHIR RESTful server, though this is the preferred approach. If the URL conforms to the structure "/[type]/[id]" then it should be assumed that the reference is to a FHIR RESTful server. The cardinality or value of this element may be affected by these constraints: ele-1, ref-1 Constraints
| ||
| type | Σ | 0..1 | uriBinding | There are no (further) constraints on this element Element idProvenance.target.typeShort description Type the reference refers to (e.g. "Patient") DefinitionThe expected type of the target of the reference. If both Reference.type and Reference.reference are populated and Reference.reference is a FHIR URL, both SHALL be consistent. The type is the Canonical URL of Resource Definition that is the type this reference refers to. References are URLs that are relative to http://hl7.org/fhir/StructureDefinition/ e.g. "Patient" is a reference to http://hl7.org/fhir/StructureDefinition/Patient. Absolute URLs are only allowed for logical models (and can only be used in references in logical models, not resources). This element is used to indicate the type of the target of the reference. This may be used which ever of the other elements are populated (or not). In some cases, the type of the target may be determined by inspection of the reference (e.g. a RESTful URL) or by resolving the target of the reference; if both the type and a reference is provided, the reference SHALL resolve to a resource of the same type as that specified. Aa resource (or, for logical models, the URI of the logical model). The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| identifier | Σ | 0..1 | Identifier | There are no (further) constraints on this element Element idProvenance.target.identifierShort description Logical reference, when literal reference is not known DefinitionAn identifier for the target resource. This is used when there is no way to reference the other resource directly, either because the entity it represents is not available through a FHIR server, or because there is no way for the author of the resource to convert a known identifier to an actual location. There is no requirement that a Reference.identifier point to something that is actually exposed as a FHIR instance, but it SHALL point to a business concept that would be expected to be exposed as a FHIR instance, and that instance would need to be of a FHIR resource type allowed by the reference. When an identifier is provided in place of a reference, any system processing the reference will only be able to resolve the identifier to a reference if it understands the business context in which the identifier is used. Sometimes this is global (e.g. a national identifier) but often it is not. For this reason, none of the useful mechanisms described for working with references (e.g. chaining, includes) are possible, nor should servers be expected to be able resolve the reference. Servers may accept an identifier based reference untouched, resolve it, and/or reject it - see CapabilityStatement.rest.resource.referencePolicy. When both an identifier and a literal reference are provided, the literal reference is preferred. Applications processing the resource are allowed - but not required - to check that the identifier matches the literal reference Applications converting a logical reference to a literal reference may choose to leave the logical reference present, or remove it. Reference is intended to point to a structure that can potentially be expressed as a FHIR resource, though there is no need for it to exist as an actual FHIR resource instance - except in as much as an application wishes to actual find the target of the reference. The content referred to be the identifier must meet the logical constraints implied by any limitations on what resource types are permitted for the reference. For example, it would not be legitimate to send the identifier for a drug prescription if the type were Reference(Observation|DiagnosticReport). One of the use-cases for Reference.identifier is the situation where no FHIR representation exists (where the type is Reference (Any). The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| display | Σ | 0..1 | string | There are no (further) constraints on this element Element idProvenance.target.displayShort description Text alternative for the resource DefinitionPlain text narrative that identifies the resource in addition to the resource reference. This is generally not the same as the Resource.text of the referenced resource. The purpose is to identify what's being referenced, not to fully describe it. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| occurred[x] | 0..1 | There are no (further) constraints on this element Element idProvenance.occurred[x]Short description When the activity occurred DefinitionThe period during which the activity occurred. The period can be a little arbitrary; where possible, the time should correspond to human assessment of the activity time. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||||
| occurredDateTime | dateTime | There are no (further) constraints on this element Data type | ||||
| occurredPeriod | Period | There are no (further) constraints on this element Data type | ||||
| recorded | S Σ | 1..1 | instant | There are no (further) constraints on this element Element idProvenance.recordedShort description When the activity was recorded / updated DefinitionThe instant of time at which the activity was recorded. This can be a little different from the time stamp on the resource if there is a delay between recording the event and updating the provenance and target resource. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| policy | 0..* | uri | There are no (further) constraints on this element Element idProvenance.policyShort description Policy or plan the activity was defined by DefinitionPolicy or plan the activity was defined by. Typically, a single activity may have multiple applicable policy documents, such as patient consent, guarantor funding, etc. For example: Where an OAuth token authorizes, the unique identifier from the OAuth token is placed into the policy element Where a policy engine (e.g. XACML) holds policy logic, the unique policy identifier is placed into the policy element. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| |||
| location | C | 0..1 | Reference(Location) | There are no (further) constraints on this element Element idProvenance.locationShort description Where the activity occurred, if relevant DefinitionWhere the activity occurred, if relevant. References SHALL be a reference to an actual FHIR resource, and SHALL be resolveable (allowing for access control, temporary unavailability, etc.). Resolution can be either by retrieval from the URL, or, where applicable by resource type, by treating an absolute reference as a canonical URL and looking it up in a local registry/repository. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| reason | 0..* | CodeableConceptBinding | There are no (further) constraints on this element Element idProvenance.reasonShort description Reason the activity is occurring DefinitionThe reason that the activity was taking place. Not all terminology uses fit this general pattern. In some cases, models should not use CodeableConcept and use Coding directly and provide their own structure for managing text, codings, translations and the relationship between elements and pre- and post-coordination. The reason the activity took place. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| |||
| activity | 0..1 | CodeableConceptBinding | There are no (further) constraints on this element Element idProvenance.activityShort description Activity that occurred DefinitionAn activity is something that occurs over a period of time and acts upon or with entities; it may include consuming, processing, transforming, modifying, relocating, using, or generating entities. Not all terminology uses fit this general pattern. In some cases, models should not use CodeableConcept and use Coding directly and provide their own structure for managing text, codings, translations and the relationship between elements and pre- and post-coordination. The activity that took place. ProvenanceActivityType (extensible) ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| |||
| agent | S | 1..* | BackboneElement | Element idProvenance.agentShort description Actor involved DefinitionAn dieser Stelle soll die verwendete Software dokumentiert werden. Über die Form der Dokumentation wird hier keine Aussage getroffen, d.h. auch eine freitextliche Angabe (agent.who.display) ist möglich. Optional können die an der Erstellung der Einwilligung beteiligten Personen und/oder Organisationen hier referenziert werden, sofern im konkreten Anwendungsfall die Referenzierung mittels signature.who nicht ausreicht. An agent can be a person, an organization, software, device, or other entities that may be ascribed responsibility. Several agents may be associated (i.e. has some responsibility for an activity) with an activity and vice-versa. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| id | 0..1 | string | There are no (further) constraints on this element Element idProvenance.agent.idShort description Unique id for inter-element referencing DefinitionUnique id for the element within a resource (for internal references). This may be any string value that does not contain spaces.
| |||
| extension | C | 0..* | Extension | There are no (further) constraints on this element Element idProvenance.agent.extensionShort description Additional content defined by implementations Alternate namesextensions, user content DefinitionMay be used to represent additional information that is not part of the basic definition of the element. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer can define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. Unordered, Open, by url(Value) Extensions are always sliced by (at least) url ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| modifierExtension | Σ ?! C | 0..* | Extension | There are no (further) constraints on this element Element idProvenance.agent.modifierExtensionShort description Extensions that cannot be ignored even if unrecognized Alternate namesextensions, user content, modifiers DefinitionMay be used to represent additional information that is not part of the basic definition of the element and that modifies the understanding of the element in which it is contained and/or the understanding of the containing element's descendants. Usually modifier elements provide negation or qualification. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer can define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. Applications processing a resource are required to check for modifier extensions. Modifier extensions SHALL NOT change the meaning of any elements on Resource or DomainResource (including cannot change the meaning of modifierExtension itself). Modifier extensions allow for extensions that cannot be safely ignored to be clearly distinguished from the vast majority of extensions which can be safely ignored. This promotes interoperability by eliminating the need for implementers to prohibit the presence of extensions. For further information, see the definition of modifier extensions. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| type | Σ | 0..1 | CodeableConceptBinding | There are no (further) constraints on this element Element idProvenance.agent.typeShort description How the agent participated DefinitionThe participation the agent had with respect to the activity. For example: author, performer, enterer, attester, etc. The type of participation that a provenance agent played with respect to the activity. ProvenanceParticipantType (extensible) ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| role | 0..* | CodeableConcept | There are no (further) constraints on this element Element idProvenance.agent.roleShort description What the agents role was DefinitionThe function of the agent with respect to the activity. The security role enabling the agent with respect to the activity. For example: doctor, nurse, clerk, etc. The role that a provenance agent played with respect to the activity. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| |||
| who | S Σ C | 1..1 | Reference(Device | Organization | Patient | Practitioner | PractitionerRole | RelatedPerson) | There are no (further) constraints on this element Element idProvenance.agent.whoShort description Who participated DefinitionThe individual, device or organization that participated in the event. whoIdentity should be used when the agent is not a Resource type. Reference(Device | Organization | Patient | Practitioner | PractitionerRole | RelatedPerson) ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| onBehalfOf | C | 0..1 | Reference(Device | Organization | Patient | Practitioner | PractitionerRole | RelatedPerson) | There are no (further) constraints on this element Element idProvenance.agent.onBehalfOfShort description Who the agent is representing DefinitionThe individual, device, or organization for whom the change was made. onBehalfOfIdentity should be used when the agent is not a Resource type. Reference(Device | Organization | Patient | Practitioner | PractitionerRole | RelatedPerson) ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| entity | S | 0..* | BackboneElement | There are no (further) constraints on this element Element idProvenance.entityShort description An entity used in this activity DefinitionAn entity used in this activity. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| id | 0..1 | string | There are no (further) constraints on this element Element idProvenance.entity.idShort description Unique id for inter-element referencing DefinitionUnique id for the element within a resource (for internal references). This may be any string value that does not contain spaces.
| |||
| extension | C | 0..* | Extension | There are no (further) constraints on this element Element idProvenance.entity.extensionShort description Additional content defined by implementations Alternate namesextensions, user content DefinitionMay be used to represent additional information that is not part of the basic definition of the element. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer can define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. Unordered, Open, by url(Value) Extensions are always sliced by (at least) url ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| modifierExtension | Σ ?! C | 0..* | Extension | There are no (further) constraints on this element Element idProvenance.entity.modifierExtensionShort description Extensions that cannot be ignored even if unrecognized Alternate namesextensions, user content, modifiers DefinitionMay be used to represent additional information that is not part of the basic definition of the element and that modifies the understanding of the element in which it is contained and/or the understanding of the containing element's descendants. Usually modifier elements provide negation or qualification. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer can define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. Applications processing a resource are required to check for modifier extensions. Modifier extensions SHALL NOT change the meaning of any elements on Resource or DomainResource (including cannot change the meaning of modifierExtension itself). Modifier extensions allow for extensions that cannot be safely ignored to be clearly distinguished from the vast majority of extensions which can be safely ignored. This promotes interoperability by eliminating the need for implementers to prohibit the presence of extensions. For further information, see the definition of modifier extensions. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| role | S Σ | 1..1 | codeBindingFixed Value | Element idProvenance.entity.roleShort description derivation | revision | quotation | source | removal DefinitionHow the entity was used during the activity. Note that FHIR strings SHALL NOT exceed 1MB in size How an entity was used in an activity. ProvenanceEntityRole (required) ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
sourceMappings
| ||
| what | S Σ C | 1..1 | Reference(ConsentManagementDocumentReference | ConsentManagementQuestionnaireResponse) | Element idProvenance.entity.whatShort description Identity of entity DefinitionIdentity of the Entity used. May be a logical or physical uri and maybe absolute or relative. whatIdentity should be used for entities that are not a Resource type. Reference(ConsentManagementDocumentReference | ConsentManagementQuestionnaireResponse) ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| id | 0..1 | string | There are no (further) constraints on this element Element idProvenance.entity.what.idShort description Unique id for inter-element referencing DefinitionUnique id for the element within a resource (for internal references). This may be any string value that does not contain spaces.
| |||
| extension | C | 0..* | Extension | There are no (further) constraints on this element Element idProvenance.entity.what.extensionShort description Additional content defined by implementations Alternate namesextensions, user content DefinitionMay be used to represent additional information that is not part of the basic definition of the element. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer can define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. Unordered, Open, by url(Value) Extensions are always sliced by (at least) url ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| reference | S Σ C | 1..1 | string | There are no (further) constraints on this element Element idProvenance.entity.what.referenceShort description Literal reference, Relative, internal or absolute URL DefinitionA reference to a location at which the other resource is found. The reference may be a relative reference, in which case it is relative to the service base URL, or an absolute URL that resolves to the location where the resource is found. The reference may be version specific or not. If the reference is not to a FHIR RESTful server, then it should be assumed to be version specific. Internal fragment references (start with '#') refer to contained resources. Using absolute URLs provides a stable scalable approach suitable for a cloud/web context, while using relative/logical references provides a flexible approach suitable for use when trading across closed eco-system boundaries. Absolute URLs do not need to point to a FHIR RESTful server, though this is the preferred approach. If the URL conforms to the structure "/[type]/[id]" then it should be assumed that the reference is to a FHIR RESTful server. The cardinality or value of this element may be affected by these constraints: ele-1, ref-1 Constraints
| ||
| type | Σ | 0..1 | uriBinding | There are no (further) constraints on this element Element idProvenance.entity.what.typeShort description Type the reference refers to (e.g. "Patient") DefinitionThe expected type of the target of the reference. If both Reference.type and Reference.reference are populated and Reference.reference is a FHIR URL, both SHALL be consistent. The type is the Canonical URL of Resource Definition that is the type this reference refers to. References are URLs that are relative to http://hl7.org/fhir/StructureDefinition/ e.g. "Patient" is a reference to http://hl7.org/fhir/StructureDefinition/Patient. Absolute URLs are only allowed for logical models (and can only be used in references in logical models, not resources). This element is used to indicate the type of the target of the reference. This may be used which ever of the other elements are populated (or not). In some cases, the type of the target may be determined by inspection of the reference (e.g. a RESTful URL) or by resolving the target of the reference; if both the type and a reference is provided, the reference SHALL resolve to a resource of the same type as that specified. Aa resource (or, for logical models, the URI of the logical model). The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| identifier | Σ | 0..1 | Identifier | There are no (further) constraints on this element Element idProvenance.entity.what.identifierShort description Logical reference, when literal reference is not known DefinitionAn identifier for the target resource. This is used when there is no way to reference the other resource directly, either because the entity it represents is not available through a FHIR server, or because there is no way for the author of the resource to convert a known identifier to an actual location. There is no requirement that a Reference.identifier point to something that is actually exposed as a FHIR instance, but it SHALL point to a business concept that would be expected to be exposed as a FHIR instance, and that instance would need to be of a FHIR resource type allowed by the reference. When an identifier is provided in place of a reference, any system processing the reference will only be able to resolve the identifier to a reference if it understands the business context in which the identifier is used. Sometimes this is global (e.g. a national identifier) but often it is not. For this reason, none of the useful mechanisms described for working with references (e.g. chaining, includes) are possible, nor should servers be expected to be able resolve the reference. Servers may accept an identifier based reference untouched, resolve it, and/or reject it - see CapabilityStatement.rest.resource.referencePolicy. When both an identifier and a literal reference are provided, the literal reference is preferred. Applications processing the resource are allowed - but not required - to check that the identifier matches the literal reference Applications converting a logical reference to a literal reference may choose to leave the logical reference present, or remove it. Reference is intended to point to a structure that can potentially be expressed as a FHIR resource, though there is no need for it to exist as an actual FHIR resource instance - except in as much as an application wishes to actual find the target of the reference. The content referred to be the identifier must meet the logical constraints implied by any limitations on what resource types are permitted for the reference. For example, it would not be legitimate to send the identifier for a drug prescription if the type were Reference(Observation|DiagnosticReport). One of the use-cases for Reference.identifier is the situation where no FHIR representation exists (where the type is Reference (Any). The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| display | Σ | 0..1 | string | There are no (further) constraints on this element Element idProvenance.entity.what.displayShort description Text alternative for the resource DefinitionPlain text narrative that identifies the resource in addition to the resource reference. This is generally not the same as the Resource.text of the referenced resource. The purpose is to identify what's being referenced, not to fully describe it. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| agent | 0..* | see (agent) | There are no (further) constraints on this element Element idProvenance.entity.agentShort description Entity is attributed to this agent DefinitionThe entity is attributed to an agent to express the agent's responsibility for that entity, possibly along with other agents. This description can be understood as shorthand for saying that the agent was responsible for the activity which generated the entity. A usecase where one Provenance.entity.agent is used where the Entity that was used in the creation/updating of the Target, is not in the context of the same custodianship as the Target, and thus the meaning of Provenance.entity.agent is to say that the entity referenced is managed elsewhere and that this Agent provided access to it. This would be similar to where the Entity being referenced is managed outside FHIR, such as through HL7 v2, v3, or XDS. This might be where the Entity being referenced is managed in another FHIR resource server. Thus it explains the Provenance of that Entity's use in the context of this Provenance activity.
| |||
| signature | S | 0..* | Signature | There are no (further) constraints on this element Element idProvenance.signatureShort description Signature on target DefinitionA digital signature on the target Reference(s). The signer should match a Provenance.agent. The purpose of the signature is indicated. The elements of the Signature Resource are for ease of access of these elements. For digital signatures (Xml DigSig, JWS), the non-repudiation proof comes from the Signature validation, which includes validation of the referenced objects (e.g. Resources) (a.k.a., Content) in the XML-Signature Detached form. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| id | 0..1 | string | There are no (further) constraints on this element Element idProvenance.signature.idShort description Unique id for inter-element referencing DefinitionUnique id for the element within a resource (for internal references). This may be any string value that does not contain spaces.
| |||
| extension | C | 0..* | Extension | Element idProvenance.signature.extensionShort description Additional content defined by implementations Alternate namesextensions, user content DefinitionMay be used to represent additional information that is not part of the basic definition of the element. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer can define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. Unordered, Open, by url(Value) Extensions are always sliced by (at least) url ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| where | S C | 0..1 | Extension(string) | Element idProvenance.signature.extension:whereShort description Optional Extensions Element Alternate namesextensions, user content DefinitionOptional Extension Element - found in all resources. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. http://fhir.de/ConsentManagement/StructureDefinition/SignatureLocation ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| id | 0..1 | string | There are no (further) constraints on this element Element idProvenance.signature.extension:where.idShort description Unique id for inter-element referencing DefinitionUnique id for the element within a resource (for internal references). This may be any string value that does not contain spaces.
| |||
| extension | C | 0..* | Extension | There are no (further) constraints on this element Element idProvenance.signature.extension:where.extensionShort description Additional content defined by implementations Alternate namesextensions, user content DefinitionMay be used to represent additional information that is not part of the basic definition of the element. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer can define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. Unordered, Open, by url(Value) Extensions are always sliced by (at least) url ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| url | 1..1 | uriFixed Value | There are no (further) constraints on this element Element idProvenance.signature.extension:where.urlShort description identifies the meaning of the extension DefinitionSource of the definition for the extension code - a logical name or a URL. The definition may point directly to a computable or human-readable definition of the extensibility codes, or it may be a logical URI as declared in some other specification. The definition SHALL be a URI for the Structure Definition defining the extension. http://fhir.de/ConsentManagement/StructureDefinition/SignatureLocationMappings
| |||
| value[x] | S | 1..1 | There are no (further) constraints on this element Element idProvenance.signature.extension:where.value[x]Short description Value of extension DefinitionValue of extension - must be one of a constrained set of the data types (see Extensibility for a list). The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| |||
| valueString | string | There are no (further) constraints on this element Data type | ||||
| type | S Σ | 1..* | CodingBinding | Element idProvenance.signature.typeShort description Indication of the reason the entity signed the object(s) DefinitionAn indication of the reason that the entity signed this document. This may be explicitly included as part of the signature information and can be used when determining accountability for various actions concerning the document. Examples include attesting to: authorship, correct transcription, and witness of specific event. Also known as a "Commitment Type Indication". An indication of the reason that an entity signed the object. SignatureTypeCodes (extensible) ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| id | 0..1 | string | There are no (further) constraints on this element Element idProvenance.signature.type.idShort description Unique id for inter-element referencing DefinitionUnique id for the element within a resource (for internal references). This may be any string value that does not contain spaces.
| |||
| extension | C | 0..* | Extension | There are no (further) constraints on this element Element idProvenance.signature.type.extensionShort description Additional content defined by implementations Alternate namesextensions, user content DefinitionMay be used to represent additional information that is not part of the basic definition of the element. To make the use of extensions safe and manageable, there is a strict set of governance applied to the definition and use of extensions. Though any implementer can define an extension, there is a set of requirements that SHALL be met as part of the definition of the extension. There can be no stigma associated with the use of extensions by any application, project, or standard - regardless of the institution or jurisdiction that uses or defines the extensions. The use of extensions is what allows the FHIR specification to retain a core level of simplicity for everyone. Unordered, Open, by url(Value) Extensions are always sliced by (at least) url ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| system | S Σ | 1..1 | uri | There are no (further) constraints on this element Element idProvenance.signature.type.systemShort description Identity of the terminology system DefinitionThe identification of the code system that defines the meaning of the symbol in the code. Need to be unambiguous about the source of the definition of the symbol. The URI may be an OID (urn:oid:...) or a UUID (urn:uuid:...). OIDs and UUIDs SHALL be references to the HL7 OID registry. Otherwise, the URI should come from HL7's list of FHIR defined special URIs or it should reference to some definition that establishes the system clearly and unambiguously. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| version | Σ | 0..1 | string | There are no (further) constraints on this element Element idProvenance.signature.type.versionShort description Version of the system - if relevant DefinitionThe version of the code system which was used when choosing this code. Note that a well-maintained code system does not need the version reported, because the meaning of codes is consistent across versions. However this cannot consistently be assured, and when the meaning is not guaranteed to be consistent, the version SHOULD be exchanged. Where the terminology does not clearly define what string should be used to identify code system versions, the recommendation is to use the date (expressed in FHIR date format) on which that version was officially published as the version date. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| code | S Σ | 1..1 | code | There are no (further) constraints on this element Element idProvenance.signature.type.codeShort description Symbol in syntax defined by the system DefinitionA symbol in syntax defined by the system. The symbol may be a predefined code or an expression in a syntax defined by the coding system (e.g. post-coordination). Need to refer to a particular code in the system. Note that FHIR strings SHALL NOT exceed 1MB in size The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| display | Σ | 0..1 | string | There are no (further) constraints on this element Element idProvenance.signature.type.displayShort description Representation defined by the system DefinitionA representation of the meaning of the code in the system, following the rules of the system. Need to be able to carry a human-readable meaning of the code for readers that do not know the system. Note that FHIR strings SHALL NOT exceed 1MB in size The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| userSelected | Σ | 0..1 | boolean | There are no (further) constraints on this element Element idProvenance.signature.type.userSelectedShort description If this coding was chosen directly by the user DefinitionIndicates that this coding was chosen by a user directly - e.g. off a pick list of available items (codes or displays). This has been identified as a clinical safety criterium - that this exact system/code pair was chosen explicitly, rather than inferred by the system based on some rules or language processing. Amongst a set of alternatives, a directly chosen code is the most appropriate starting point for new translations. There is some ambiguity about what exactly 'directly chosen' implies, and trading partner agreement may be needed to clarify the use of this element and its consequences more completely. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| when | S Σ | 1..1 | instant | There are no (further) constraints on this element Element idProvenance.signature.whenShort description When the signature was created DefinitionWhen the digital signature was signed. This should agree with the information in the signature. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| who | S Σ C | 1..1 | Reference(Device | Organization | Patient | Practitioner | PractitionerRole | RelatedPerson) | There are no (further) constraints on this element Element idProvenance.signature.whoShort description Who signed DefinitionA reference to an application-usable description of the identity that signed (e.g. the signature used their private key). This should agree with the information in the signature. Reference(Device | Organization | Patient | Practitioner | PractitionerRole | RelatedPerson) ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| onBehalfOf | S Σ C | 0..1 | Reference(Device | Organization | Patient | Practitioner | PractitionerRole | RelatedPerson) | There are no (further) constraints on this element Element idProvenance.signature.onBehalfOfShort description The party represented DefinitionA reference to an application-usable description of the identity that is represented by the signature. used when the signature is on behalf of a non-signer. The party that can't sign. For example a child. Reference(Device | Organization | Patient | Practitioner | PractitionerRole | RelatedPerson) ConditionsThe cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| ||
| targetFormat | 0..1 | codeBinding | There are no (further) constraints on this element Element idProvenance.signature.targetFormatShort description The technical format of the signed resources DefinitionA mime type that indicates the technical format of the target resources signed by the signature. "xml", "json" and "ttl" are allowed, which describe the simple encodings described in the specification (and imply appropriate bundle support). Otherwise, mime types are legal here. The mime type of an attachment. Any valid mime type is allowed. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| |||
| sigFormat | 0..1 | codeBinding | There are no (further) constraints on this element Element idProvenance.signature.sigFormatShort description The technical format of the signature DefinitionA mime type that indicates the technical format of the signature. Important mime types are application/signature+xml for X ML DigSig, application/jose for JWS, and image/* for a graphical image of a signature, etc. Note that FHIR strings SHALL NOT exceed 1MB in size The mime type of an attachment. Any valid mime type is allowed. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
| |||
| data | S | 0..1 | base64Binary | There are no (further) constraints on this element Element idProvenance.signature.dataShort description The actual signature content (XML DigSig. JWS, picture, etc.) DefinitionThe base64 encoding of the Signature content. When signature is not recorded electronically this element would be empty. Where the signature type is an XML DigSig, the signed content is a FHIR Resource(s), the signature is of the XML form of the Resource(s) using XML-Signature (XMLDIG) "Detached Signature" form. The cardinality or value of this element may be affected by these constraints: ele-1 Constraints
|
Beispiele
Beispiel für Provenance bezogen auf 1 Dokument (Scan) und 1..n Unterschriften
Die Provenance beschreibt, dass das QuestionnaireResponse (target) seine Daten aus dem Scan (DocumentReference -> entity.what) bezogen hat.
Beispiel für Provenance bezogen auf 1..n ausgefüllte Fragebögen und OHNE Unterschriften
Die Provenance beschreibt, dass das eine Consent-Resource (target) erzeugt wurde aus Daten von 1..n QuestionnaireResponses (entity.what), beispielsweise im Fall von ResultType consent-status oder policy.
